The next guinea pig is Maximus bootkit based on notorious Mebroot/Sinowal/MaosBoot. This bootkit is dated by 2008. Its dropper waits some time (about a hour) to complete installation. Then it reboots the computer. It refuses to work on our Windows 7 test system, but perfectly works on Windows Server 2003. Let’s start Hypersight Rootkit Detector’s monitoring on the infected system:


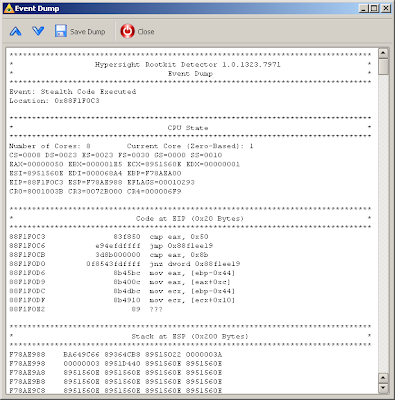
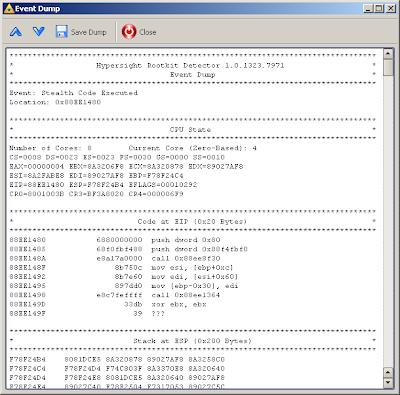
There are some typical code pieces of this rootkit shown below.
The code called by patched call of tcpip!IPRcvPacket:

And finally, the piece of the bootkit’s image in the memory (“MaOS” is a signature typical for Mebroot bootkits):


No comments:
Post a Comment