Let us check out the new facilities of Hypersight Rootkit Detector using a sample of TDL3 rootkit. This epic rootkit was a nightmare for virus analysts recently.
Testing environment: Windows 2003 SP2 system, Intel Core 2 Duo E6700 processor. The initial conditions of the test: Hypersight RD 1.0.1233.5523 beta is installed, PC has been rebooted and “Start” button is pressed inside of the UI.
After starting the sample we can see that Hypersight has found covert code execution on the processor.

Covert code detected by Hypersight
We can observe several events. Each event is the execution of covert code on a single page (pages are 4096 bytes long in IA32/IA32e architecture). After pressing “Save All” button we can save the rootkit’s profile of execution to the compresed binary dump. Also we can press “View Dump” button and view each event dump in the separate window. Each dump contains couple of memory regions with the code and the stack, processor state and loaded kernel modules at the moment of event occurring. The format of event dumps is open. We will publish open source tool for decoding dumps soon.




Dump of code launched from TDL3 dropper
If you have reverse engineering skills, you can check out the stack for return address and see that the code has been launched from the newly loaded kernel module (3.tmp).
Another typical dump: a hook installed on IRP callback. In this case, one of registers in the dump usually points to driver object (DRIVER_OBJECT) MajorFunction callback of which has been hooked.
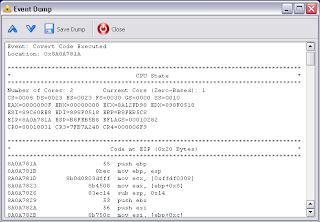
Dump of IRP hook installed by TDL3. ESI points to DRIVER_OBJECT structure
